SHARE THIS POST
Recent Posts
FOLLOW IAASTEAM
IAASTEAM POST INFORMATION
MTK META Utility V61 Primary Boot Region Brick Fix Tool Free Download
MTK META Utility V61
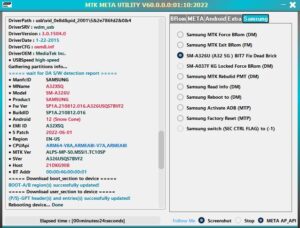
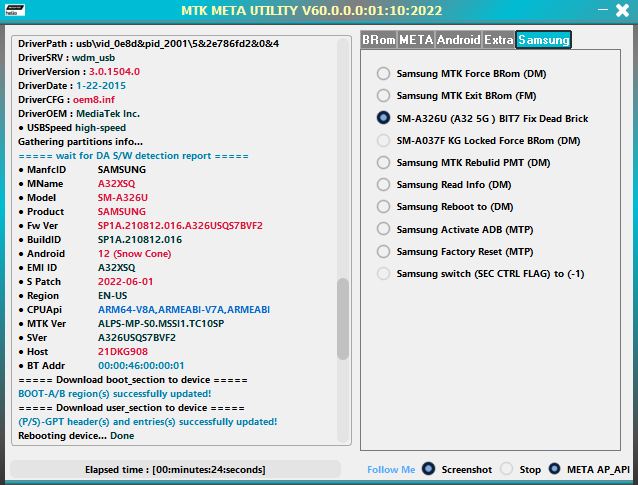
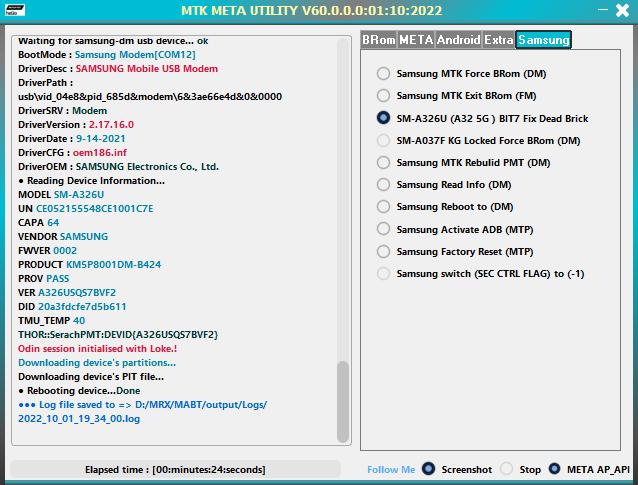
Added Samsung A32 5G (A326U) BIT 7 any Rev, fix bricked
(stuck at BROM port after service or try to unlock with other tool, (corrupted/damaged)
Primary Boot Region Container (LU-0) & USER_PART PMT (P-GPT).
3 files stored Inside software resources will be used to service your device (LU-0 & P-GPT & PIT).
This software is provided ‘as-is’, without any express or implied warranty.
In no event will the authors be held liable for any damages arising from the use of this software, and
can be only used for legal servicing and maintenance of mobile phones, and must not be used for illegal purposes.
-USE it at your own risk.
MTK META Utility V61 :
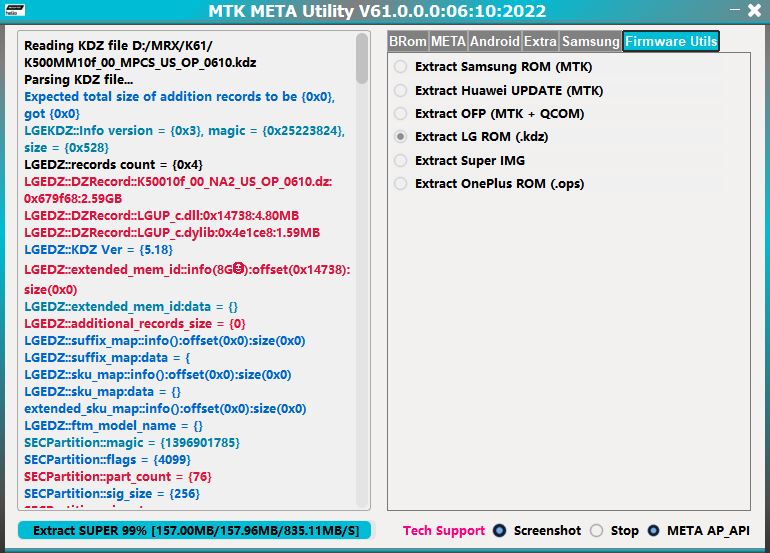
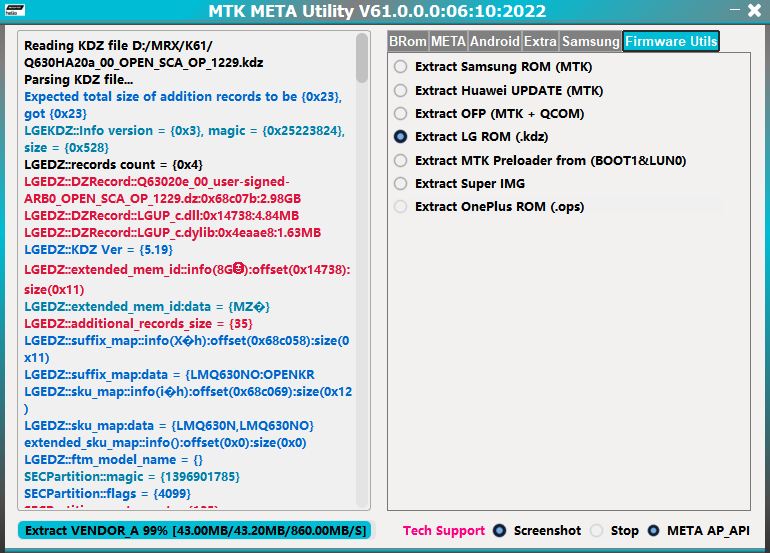
– Added LG DKZ direct (Extract/Decrypt) to raw images.
Supported KDZ formats and types :
– LGE KDZ v1 – v2 – v3 (MediaTek & Qualcomm).
– Z-Library compressed (zlib) default.
– Z-Standard compressed (zstd) a fast lossless compression algorithm
(other tools doesn’t handle this compression type very well).
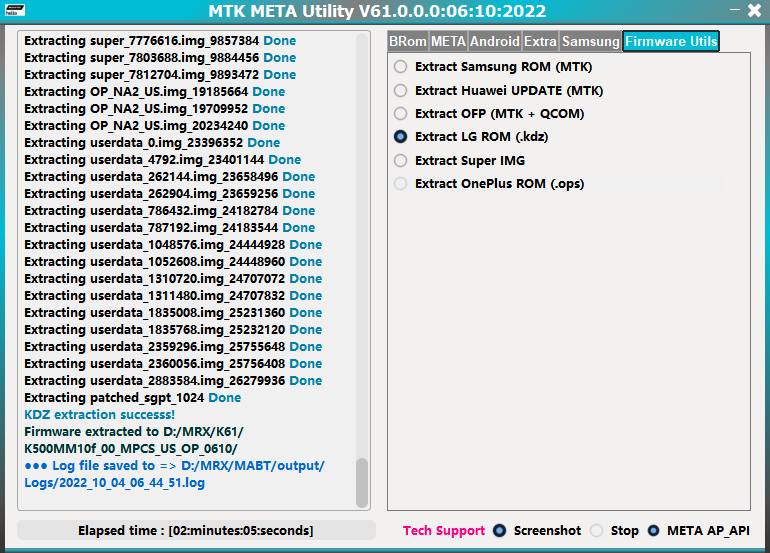
– Extraction now will be to default raw images,
scatter creation and (merge/combine) sparse (system/vendor/product/super) files,
multiple chunks, will be added in the version.
– However, you were still able to do it manually,
convert pgpt.img to scatter and add items to the scatter file &
Extract preloader IMG from the extracted raw preloader &
and use ext4_tools to (merge/combine) the extra chunks.
Some of the tested files :
– LG K51 (K500MM10f_00_MPCS_US_OP_0610.kdz)
– LG K61 (Q630HA20a_00_OPEN_SCA_OP_1229.kdz)
– LG Stylo 6 (Q730MM10l_00_MPCS_US_OP_0908.kdz)
– Added (Extract/Split) preloader IMG from BOOT_REGION and convert to flash-able preloader,
supported types eMMC & UFS Preloader (EMMC_BOOT & UFS_BOOT, COMBO_BOOT)
– Please let me know what (low-level) tasks would be helpful if we added in the
upcoming versions, we welcome any (requests & recommendations) about
firmware packages extraction, you have any type of encrypted file format
need to be extracted and used to service the mobile phones only, let us know.
– Software GUI Increased & fixed the compatibility with almost all screens
– Developers can request the (QT/C++) source code for the extraction algorithm.
MTK META Utility V60 Note – By Developer
Hello, good morning and i hope you’re all doing well :
Note : It’s about VIVO September (BETA/TRAIL) update, not August update,
in August update there were some ways to get Boot-ROM port : D
– Regarding VIVO MTK devices with MT6765 chipset, they have rolled out an update,
which disable Boot-ROM completely by FUSE, same as recent (Samsung visible [SEC CTRL] flag case).
– Undoubtedly, the updates may not be without some (side effects/damages),
considering the Boot-ROM code set to be fundamentally and
definitively approved by the phones (manufacturers/after-sales services).
– As expected, we have seen they have the ability to change the registered DA signature in
preloader code by simple hot-patch, and maybe they will manage to do the same for Boot-ROM mode
(even after the exploitation and bypass vendor security step) in the near future maybe, just assuming
they’re considering the replacement for the already burned fuses and registers which affect the
(early registered op-code), and no way to replace it with (hot-patches), means in near future even
if you managed to get Boot-ROM (Emergency Download mode) somehow the
(Boot-ROM Auth vulnerability – voltage glitching) might be patched as well.
– The FUSE can’t be reverted, because it’s BIT registers & e-FUSES control the SoC with a
special flag SET by the (Manufacturer/OEM), to be (handled/controlled) by (RPMB/FUSE/SoC bounded)
MTK META Utility V60
It depends on many factors known to the (manufacturer/source code writer).
– We all know the idea of the HW TEST-POINT in general for mobile (phones/test-boards),
which is *preventing the CPU from detecting the MEMORY forced by shorting any of the
important data lines which used for data (transfer/connection/configure) to the Ground* for FPGA setup case,
so blocking the CPU from detecting the MEMORY wouldn’t help to get
(Boot-ROM/Preloader port – any U-ART configure/handler), means
TEST-POINT is useless in case if the e-FUSES were activated.
– The googled definition of the TEST-POINT is (In the world of electronics,
a TEST-POINT is a gate or point that has a vital function as a single track or point as a tester as well as a
protection key for the overall performance of the module or digital electronic device).
– All this information based on my recent research, and my little humble background
of hardware stuffs in general, and might be (right/wrong) in some cases, if so please correct me.
Just for Info :
August patch (01.08.2022) can be handled somehow by downgrading the security,
but September patch [(01.09.2022) – (06.09.2022)] no way to handle because of EFUSES,
no way to get bootrom port under any condition.
 Skip to content
Skip to content